
One of the reasons that intruders are successful is that most of the information they acquire from a system is in a form that they can read and comprehend. Intruders reveal the information to others, modify it to misrepresent an individual or organization or use it to launch an attack. One solution to this problem is, to use steganography.
It is a technique for hiding information in digital media. Unlike cryptography, it is not to keep secret from others from knowing the hidden information but it is to keep others away from thinking that the information even exists.
Steganography is the practice of hiding private or sensitive information within something that appears to be nothing out to the usual user. Steganography is often confused with cryptology because the two of them are similar in the way that they both are used to protect important information.
The difference between two is that steganography involves hiding the information so it appears that no information is hidden at all. If a person or persons view the object that the information is hidden inside, he or she will have no idea that there is any hidden information, therefore the person will not attempt to decrypt the information.
What steganography essentially do is exploiting human perception, human senses are not trained to look for files that have information inside them. The most common work of steganography is to hide a file inside another file.
The art of detecting Steganography in a file is referred to as Steganalysis. To put is simply Steganalysis involves detecting the use of Steganography in the file. It does not deal with decrypting the hidden information inside of a file, just discovering it.
Steganography become more important as more and more people join the cyberspace revolution. Steganography is the art of concealing information in the ways that prevent the detection of hidden messages. Steganography includes a database of secret communication methods that hide the message from being seen or discovered.
Due to the advancement in technology, most of the information is kept electronically. Consequently, the security of information has become a fundamental issue today. Besides cryptography, steganography can be employed to secure confidential information. In cryptography, the message or encrypted message is embedded in a digital host before communicating it through the network, thus the existence of the message is unknown.
Besides hiding data for confidentiality, this approach of information hiding can also be extended to copyright protection for digital media resources: audio, video and images.
The growing modern communications need the special means of security especially in the case of the computer network. The network security is becoming more important as the number of data being exchanged on the internet has increased these days. Thus, confidentiality and data integrity are needed to be protected against unauthorized access and use. This has resulted in a great growth in the field of information hiding.
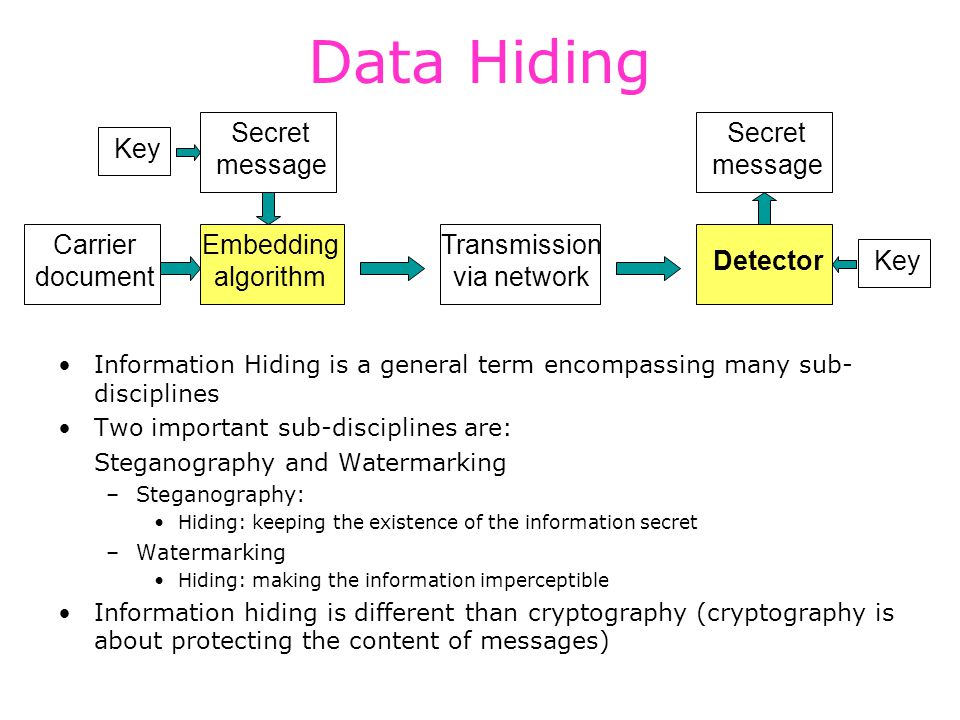
Information hiding is an emerging research area nowadays, that encompasses applications such as copyright protection for digital media, watermarking, fingerprinting, and steganography.
Steganography hides the secret message within the host data set and presence is imperceptible and is to be reliably communicated to a receiver. The host data is purposely corrupted, but in a secret way, designed to be invisible to an information analysis.
There are many means that can be used to detect Steganography such as:
Viewing the file and comparing the file to another copy of the file found on the Internet (Picture file). There are usually multiple copies of images on the internet so you may want to look for several of them and try and try to compare the suspect file to them.
For example if you download a JPEDfile and your suspect file is also a JPED one and the two files look almost identical apart from the fact that one is larger than the other one, it is most probable that you may suspect file has hidden information inside of it.
Steganography is a really interesting and outside of the mainstream unlike cryptography and system administration that most of us deal with every day. Since ancient times, man has a desire to communicate covertly. Steganography, like cryptography, will play a great role in the future of secure communication in the “digital world”.
Also read about:
Keep an Eye on Your Employees with Windows Spy Software
Top 10 Emerging Technologies that will shape the future
A MOVE TOWARDS UNDERWATER WIRELESS SENSOR NETWORKS








